ATM Security
Security of automated teller machines (ATMs) is not a very widely discussed topic. So, does it mean then, that ATMs are safe? Our expert team conducted penetration testing on various types of ATMs and is therefore able to objectively assess the issue. The conclusions may surprise you.
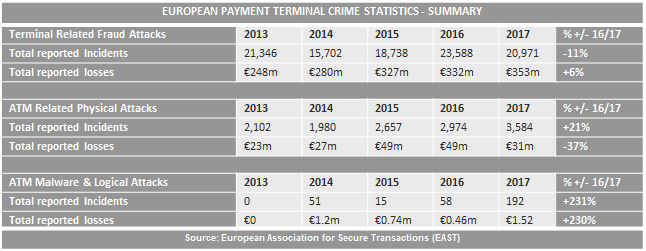
Majority of us encounter ATMs as a regular part of our daily lives. At the time when an ATM is fully filled (so-called refill), it contains more than one million Czech crowns. This makes it an attractive target for criminals and at the same time, places considerable demands on security. The number of attacks on terminal services and ATMs worldwide is continuously growing. According to EAST (European Association for Secure Transactions) statistics, the overall increase in physical attacks on ATMs between 2016 and 2017 was greater by 21%. And attacks using malware increased even more, by 231%. There are more details provided in the table below. Most of the general public considers ATMs to be highly secure devices. So what is the real status of their security today?
For many years, skimmers – special devices connected to steal data from bank cards had presented the biggest threat to the ATM clients and owners. However, attacks became gradually more sophisticated with time. 2014 was labelled as the year of malware called Tyupkin, which became one of the first well-known examples of malware targeting just that – ATMs. A Russian hacker group was probably behind its development, and it had the most considerable impact on the ATMs in the Russian Federation.
In 2015, the Carbanak gang was uncovered. They were able to execute a complete withdrawal of all cash from ATMs by compromising the bank’s infrastructure and exploiting errors in its implementation. Both examples of the attacks mentioned here were made possible by exploiting several vulnerabilities in the ATM security technology and in their infrastructure. Later on, this type of attack became known as Money Jackpotting, i.e. situation when an attacker infected an ATM with malware gradually completely emptying the ATM’s vault, thus giving the attacker all the cash without any authentication.
This new threat was more than enough motivation for the banks to start taking the security of their ATMs seriously. In recent years, we and our colleagues in AEC, have executed several ATM penetration testing projects for banks in the Czech and Slovak Republic. Therefore, we proceed from direct experience with such testing. One of the main goals was to verify the resilience of ATMs to the Money Jackpotting attack described above. And the result was that none of the tested types of ATMs were resistant to this kind of attack.
How does this thing work then?
It is important to realize that an ATM is nothing but a normal computer. However, what distinguishes it from a normal computer are the peripherals (typically connected with USB). These can be, for example, an encrypted PIN pad, a camera and, most importantly, a dispenser. The dispenser is the part of the ATM which, after verification, will give you the cash you required. Like any computer, an ATM has its own operating system. However, in case of an ATM, it is not an extra secure Linux or a specially modified version of Windows.
ATMs run on standard desktop versions of Windows, alas, not on the latest versions. A significant number of ATMs are still controlled by the Windows XP operating system, launched all the way back in 2001. And no need to point out that Microsoft has already terminated all support for this system. Fortunately, at present, this ratio is gradually changing in favour of the Windows 7 operating system, however, the share of Windows XP is still quite significant. Utilization of outdated systems designed for home usage rather than for running critical applications does not contribute much to the ATM security.
So how to go about Money Jackpotting?
Now, let's have a bit deeper look at the nature of the attack. Malware for ATMs almost always communicates through the XFS layer (eXtension for Financial Services)[5]. The publicly available and described XFS standard allows the computer located inside an ATM to communicate with the bank’s infrastructure and the hardware units processing cash and credit operations. At the same time, it provides independence from the used technical equipment by various companies such as Wincor or Diebold Nixdorf (card reader, special printers, PIN pad, dispenser, etc.).
The fundamental issue is that XFS, in the most common versions used by today’s ATMs, does not require any permissions/authentication for the processed orders. As a result, any application installed or running on the ATM can issue commands to any of the ATM's hardware units (also referred to as ATMs), including a card reader or dispenser. The following figure shows it in more details:
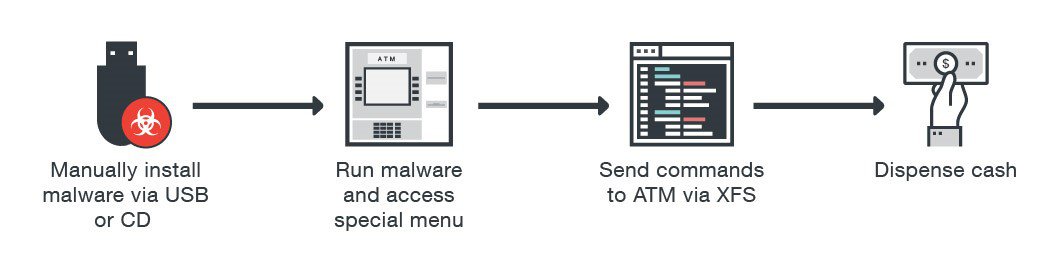
When the malware successfully infects the ATM, it gains almost unlimited possibilities of its control:
- It can modify the PIN pad including the card reader to a “native” skimmer and capture data from the payment cards.
- It can “order” the dispenser to release all cash from the ATM’s vault.
And the second possibility mentioned above is the actual reason for the Money Jackpotting attack, when the attacker entirely avoids the need to insert the card into an ATM, PIN authentication, or verification of the account balance. He issues an order to release all the cash directly on the lowest layer. We are regularly able to execute and demonstrate this kind of attack during our penetration testing activities.
Physical security
In several recent famous and investigated cases, criminals did not have to use malware at all to infect ATMs through the bank's network which the ATM is connected to. An insufficient physical security of the ATMs is at fault here since it makes the attacks much easier. ATMs are often located and installed in a way allowing any third party to easily gain physical access to the computer inside the ATM or to the network cable connecting the device to the network.
By gaining a partial or total physical access to the ATM, the potential attackers can achieve in particular:
- Installation of their own hardware device inside the ATM, which then allows attackers to remotely access and conduct the aforementioned Money Jackpotting attack. Small single-board computers the size of a payment card, such as the Arduino or Raspberry PI, are suitable for this purpose.
- Connecting the ATM to a fraudulent processing centre controlled by the attacker handling the processing of commands for individual hardware units, in order to fake and send arbitrary commands.
Although it is theoretically possible to protect the connection between ATMs and the processing centre, in reality, measures such as SSL/TLS encryption are often not implemented or are incorrectly configured. When speaking about physical security, we cannot leave out the "brute force" attacks, when an attacker takes an entire ATM or safe by force. The use of capsules with protective dye can be a protection against this type of attack, however, not all ATMs use them.
How to defend ATMs?
However, it is a sad reality, that despite the current vendor’s efforts to develop ATMs with enhanced security features, many banks continue using older unsecured models, which makes them ideal targets for attackers who are actively challenging the security of these devices.
Although security issues are most likely affecting a number of ATMs around the world, this does not mean that the situation could not be significantly improved. ATM vendors as well as banks can reduce the risk of an attack on the teller machines by applying the following measures:
- Eliminating all ATMs with unsupported operating system (Windows XP);
- Implementing more recent version of the XFS layer requiring authentication for calling critical operations (essential protection against Jackpotting attacks);
- Implementing encryption of communication and integrity check of the data transferred between individual hardware units and the computer inside the ATM.
Regular ATM security testing together with an ever-increasing number of attacks, which are becoming more sophisticated year after year, both contribute to the solving of security issues. However, in everyday practice, implementation of new protective measures can be a time-consuming and costly process, especially if the operator has an extensive ATM network.
Nevertheless, when it comes to ATM security, it seems that better days are coming. But it will take several more years before we can say that ATMs are really highly secured devices.



