Red Teaming – Red Vs. Blue, Evolution in Penetration Testing
Is Red Teaming the next generation of penetration testing? Is it a replacement or an add-on to penetration testing? Is this an evolution? Let’s draw a clear comparison of these two services and then an explanation what Red Teaming really is and what methodologies can be used to formalize it.
The term “penetration testing” has probably been heard of by everyone with a bit of knowledge moving in the world of IT and especially its security branch. Penetration testing is generally described as simulation of an attack on a specified section of IT. The subject of penetration testing is always a specific isolated part of the company's IT ecosystem, such as a web application, desktop application, or network infrastructure. The word “isolated” in the sentence above should be underlined twice. Because the greatest weakness of penetration testing lies exactly in this isolation. Results of periodical executions of these tests can provide us with an information that all security risks have been reduced to an acceptable level and that the tested system is resistant to attack.
Nevertheless, what the results of penetration testing will not tell us is the fact that the system can be compromised either by sending an e-mail with malware attachment to its administrator, or that it is possible to get to the data by compromising a totally different system, which however shares a repository with the original one, etc. Simply put, penetration testing is narrowly focused on a specific area and, by definition, it is not able to cover the interconnected complexity of the company’s ecosystem and the resulting risks.
Although security expenses in enterprises are constantly increasing, they are still targeted by sophisticated attacks. We can mention for example recent affairs involving Sony Pictures, Equifax, Deloitte, or British Airways. All these cases involved a major leak of sensitive data and the resulting damage to the company's reputation. Moreover, we are more and more often encountering attacks by government-sponsored hacking groups with espionage or sabotage being usually the main goal. This only increases the demand for a service providing a comprehensive security assessment against an external threat.
And this is where the so-called Red Teaming enters the game. Its name is derived from the term “Red Team”, which is a name given to a team of experienced ethical hackers leading a simulated attack while utilizing the same sophisticated means as real-life hackers. Red Teaming covers a very wide range of attack vectors and targets people, technologies, as well as physical assets. In addition to attempting a penetration by exploiting the vulnerabilities in a given technology, it takes advantage of the means of social engineering, gaining information with open-source intelligence (OSINT, dumpster diving), or physical penetration.
A so-called Blue Team standing on the target company’s side. This is an expert team taking care of the prevention, detection, and resolution of cyber incidents. Its aim is to do everything in their power to prevent the attack from succeeding and in the event the attack has already succeeded, then to discover it as quickly as possible, stop it, and prevent its recurrence. In today’s bigger companies, this usually means either a Security Operations (SOC) department or a Cyber Defence Centre (CDC).
Red Team vs. Blue Team
The roles of the Read Team and the Blue team are asymmetrical. In the initial phase, when the attacking team tries to penetrate the internal network protected by the defending team, the Red Team has the upper hand. The Blue Team needs to secure each one of the many potential attack vectors and this range can be really quite extensive. On the contrary, for the attacking team, it is enough to find only one vulnerability, one mistake, or to misuse the trust of only one employee, and they have gained an access to the network.
However, the situation changes right at this moment. The defending team is gaining the advantage. The attacking team ventures on the unknown territory of an internal network fully controlled by the Blue Team. The moment that Red Team makes a first mistake, starts behaving too “loudly”, activates a honeypot, or attracts attention to its activity in some other way, the Blue Team will unmercifully push them out of the internal network and the Red Team’s work starts all over again. A comparison with the imaginary game of cat and mouse is then more than appropriate here.
In the event the Red Team enters the Blue Team’s field, what is really its goal? The goal is to come unseen and obtain the so-called Flag, which is defined together with the client at the beginning of the Red Teaming exercise. For example, it can mean access to a certain segment of the internal network, access to a specific server or data prepared in advance in the database, physical access to the server room, theft of a laptop, or installation of a HW backdoor. The principle is to define the Flag in a way which after it has been achieved would allow to pronounce that the security at the technical, physical, and procedural level is not sufficient to prevent targeted infiltration from the outside. The resulting report includes a detailed analysis and description of the entire attack including dead ends or failed infiltrations, together with the proposed for successful defence across various sections.
It follows from the above that in order to achieve results as close to reality as possible, it is necessary to keep the employees of the target company, and especially the people in IT departments (IT Operations, SOC, CDC), in the dark when it comes to Red Teaming exercises. On the client’s side, only a small group of people, the so-called White Team, knows about the Red Teaming in progress. This team provides cooperation during the service delivery process. If agreed, then the attacks can take place also outside working hours and then it is essential for the contact person to be available at all times. In the case of physical intrusions, members of the Red team receive a so-called Get Out of Jail Free card, which they can prove if they are successfully detected. If physical penetration is included, the Red Team members get the so-called Get Out of Jail Free card, which they use to prove their identity in case they are successfully detected.
| Penetration testing | Red Teaming |
|---|---|
| Methodical approach | Flexible approach |
| Strictly limited scope | Unlimited scope |
| Usually takes 1 to 3 weeks | Usually takes 1 to 3 months |
| Announced | Secret, only White Team knows about it |
| The aim is to identify the vulnerabilities in a specific area | The aim is to identify the resistance of the entire environment against attack |
Cyber Kill Chain
The same as there are methodologies for the governing of penetration testing (OWASP, PTES, OSSTMM, …), there are frameworks which can be used both for the prevention of attacks by the Security Operations Center or, on the other hand, by the Red Team to describe and execute the attacks. This includes frameworks such as Cyber Kill Chain (CKC) developed by Lockheed Martin, Unified Kill Chain, or MITRE ATT&CK. We will present the CKC Framework due to its straightforwardness. The rest of the frameworks will be discussed in following articles.
CKC describes seven successive activities which must be done for the attack to succeed. The Blue Team’s task is to disrupt this chain of events, while the Red Team is trying to successfully finish each one of these attack activities.
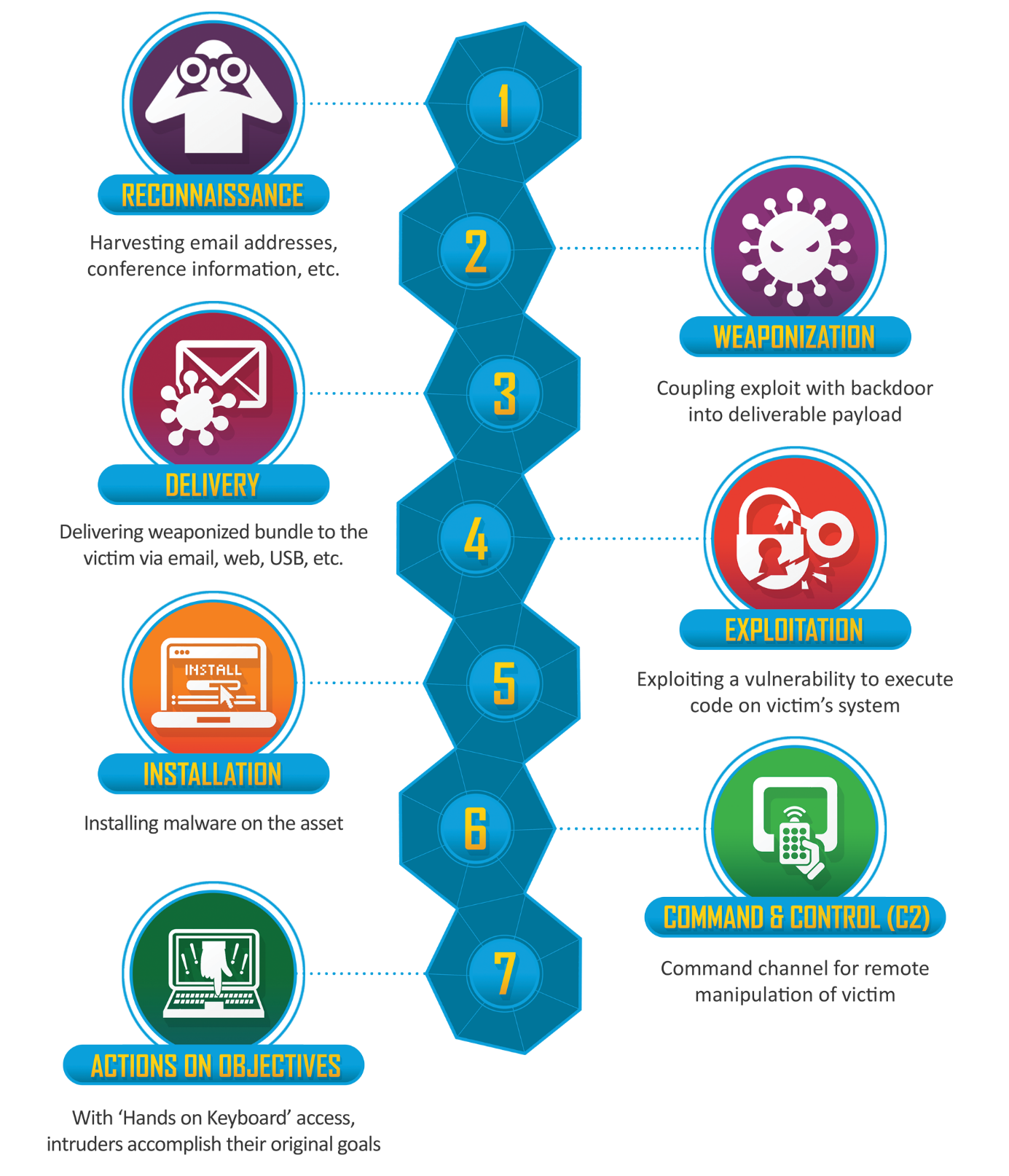
Reconnaissance
The research phase. Red Team uses open-source as well as non-public resources to obtain as much information about the target as they can. They utilize techniques such as Open-source intelligence (OSINT), reconnaissance of Social Networks or tools such as Maltego, Shodan or ZoomEye. Gathering personal information about employees (name, e-mail, phone number etc.) and information on the implemented technologies and services exposed to the Internet is also included.
Weaponization
In this preparation phase, the Red Team develops a malware tailored to the given target based on the findings from the previous phase. They use own in-house techniques for the obfuscation of the code and used exploits. The aim here is to minimize the risk that the offensive software will be detected by antimalware means in the target network.
The so-called baits are prepared for the purposes of social engineering – documents (pdf, docx, …) containing the offensive code. Exploits of the known or unknown (zero-day) vulnerabilities, document macros, or Dynamic Data Exchange (DDE) are used as well.
Delivery
This is the phase where the attacks as such are launched. Social engineering attacks can include sending e-mails with infected attachments (phishing), contacting employees over the phone (vishing), interacting on Social Networks, or using offensive USB devices (baiting) such as RubberDucky, Bash Bunny, or Raspberry Pi.
At the same time, attacks on external infrastructure and exposed services, such as web, mail and DNS servers or VPN endpoints, are launched. The phase includes also an attack on the employee and guest Wi-Fi networks.
Exploitation
This phase indicates that the penetration has been successful. It can mean the misuse of a technical error in the form of an exploit against an external infrastructure or a Wi-Fi network, or a human error misused within social engineering, when the target company employee executes the offensive code prepared by the Red Team and delivered in the preceding phase.
Installation
Red Team has been successful in compromising a server or an endpoint (user workstation or mobile device) and secures a persistent access. In the case a web server is compromised, for instance, then persistence can be achieved with a webshell. In case of an endpoint, we speak about a backdoor that is automatically launched at start. On a Windows workstation, this can be achieved, for example, by running the backdoor as a system service or by modifying AutoRun keys within the registry. This type of malware is deployed in the network as a bridgehead for further attacks inside the internal network.
Command and Control
The malware deployed in the previous phase starts communicating with the Red Team server over the Internet. The Command and Control (C2) server is used for remote control of malware in the network, usually through the HTTP(s) or DNS protocol. That is because with these protocols, there are minimal problems with outgoing communication directed from the internal network to the Internet. There is one dilemma the Red Team faces here, and that is whether to use one of the open-source C2s (Empire Framework, Pupy, Koadic, …), commercial C2s (Cobalt Strike), or their own in-house solution.
Actions on Objectives
As soon as the Red Team gains persistent remote access to the target internal network, it will begin with activities aimed at achieving the predefined goal - obtaining a Flag. These activities include internal network reconnaissance, lateral movement, collection of user accounts and passwords, escalation of privileges and later, in the final phase, data exfiltration.
On the Czech and Slovak market, the Red Teaming is an up and coming service. However, in few years, it will be seen as a standard service, in the same way as penetration testing is seen today. Red Teaming is not intended to completely replace penetration testing, but rather offers a comprehensive additional service in response to modern sophisticated cyberattacks.



