Wiretapping
How easy is eavesdropping on network traffic between two computers? Would it be enough to simply cut and split the network cable? Wiretapping is a way to connect to a network cable and start eavesdropping. During eavesdropping, the original communication is "copied" to the attacker's eavesdropping device. The transmitted data is not modified in any way.
Attack in theory
The attack is targeted directly at the physical medium, i.e. the cable, and is therefore implemented at the lowest layer of the ISO/OSI model – the physical layer. This makes this activity invisible to other layers. However, reduction in speed and collision might occur, therefore it is not advisable to conduct eavesdropping on long cables.
Different types of cables are used for data transmission, in most cases, it is twisted pair cabling.
We distinguish cabling according to various parameters.
Classification on the basis of construction:
- Unshielded Twisted Pair (UTP)
- Shielded Twisted Pair (STP)
Classification on the basis of speed:
- Fast Ethernet (100BASE-TX) - category 5E
- Gigabit Ethernet (1000BASE-T) - category 6E
Further division of the physical media is not important for the needs of the attack described below.
Individual wire pairs are color-coded. There are 2 types of wiring in the connector, namely T568A and T568B. In the Czech Republic, we most often come across the T568B type. The manner of connection of individual wires of the T568B type is described in the figure below:
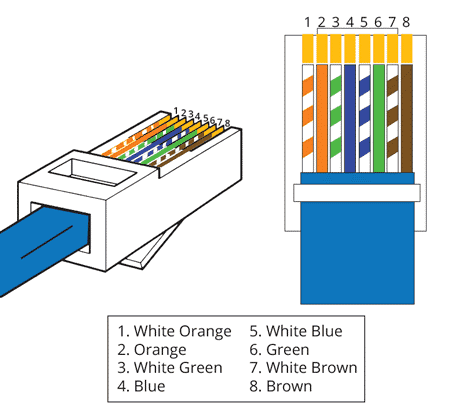
In case of the 10 Mb and 100 Mb Ethernet transmission, only two pairs of wires are used for data transmission, namely the orange one (connected to pins 1 and 2) for transmission (Tx) and green one (connected to pins 3 and 6) for reception (Rx).
Eavesdropping procedure
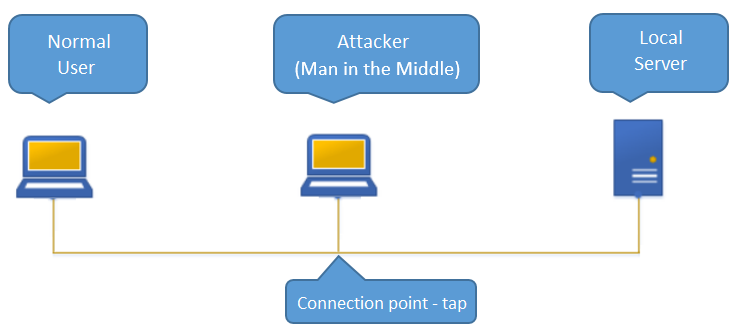
Eavesdropping takes place only on one pair of wires, which means it is a half-duplex. This is because the sniffers only work in one direction. For full-duplex, it is necessary to use 2 connections (taps) and two network cards. In our case, we will use the orange pair Tx+ and Tx- for eavesdropping, which means that we will intercept packets sent by the user to the server.
The connection scheme will be as follows:
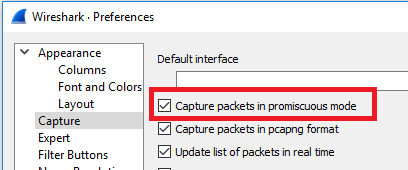
To eavesdrop on the traffic, it is necessary to set the network card to the so-called promiscuous mode – a mode for receiving communication without transmitting data. We will use the Wireshark network sniffer, which takes care of this setting automatically:
This type of eavesdropping procedure only works on Fast Ethernet networks and lower. Gigabit Ethernet networks use a different pair assignment and require all four pairs to be connected for transmission.
Implementation in a lab
Let’s consider a basic connection, where a normal user is connected by a network cable to a network element (switch, router, ...). In our case, we used a standard TP-Link TL-WR841N router, a laptop with the Windows 10 operating system and a standard EMOS cable - CAT5e UTP for demonstration:

First, we carefully cut the cable so as not to damage the insulation of the wires. Then we cut it lengthwise, an electrician's knife with a curved tip is the best one for this job. We leave the cut protective cover on the cable so that we can put it back at the end and cover up the cut place:
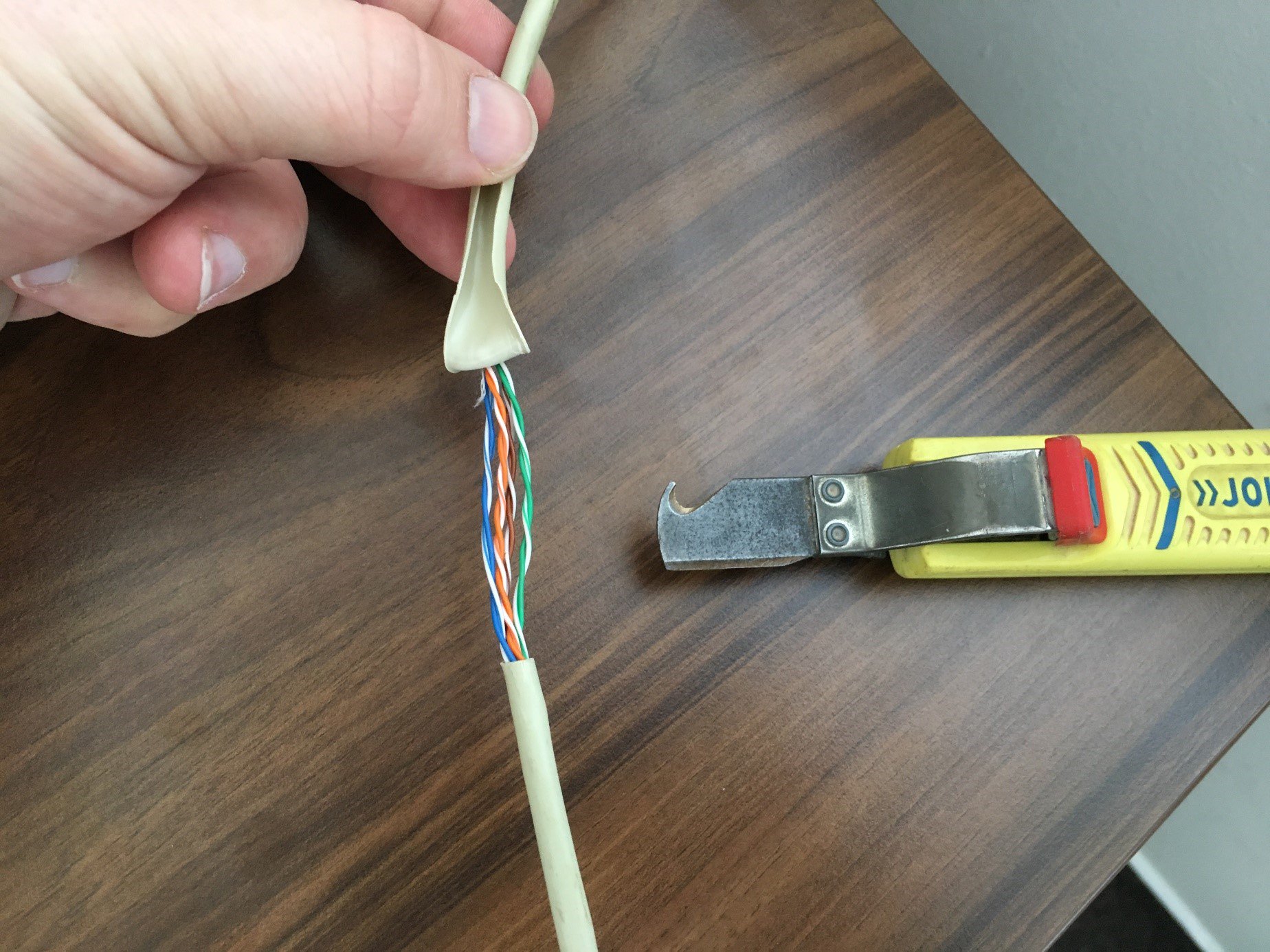
We will be eavesdropping on the outgoing communication, so we will untangle the orange pair. The wires are twisted only to one side, so they cannot be untangled, but the loops can be tightened at one end, which creates an eye large enough for the deployment of a data socket with an RJ45 port (keystone). The pins on the data socket for inserting the wires are color. In our case it was a type B connection:
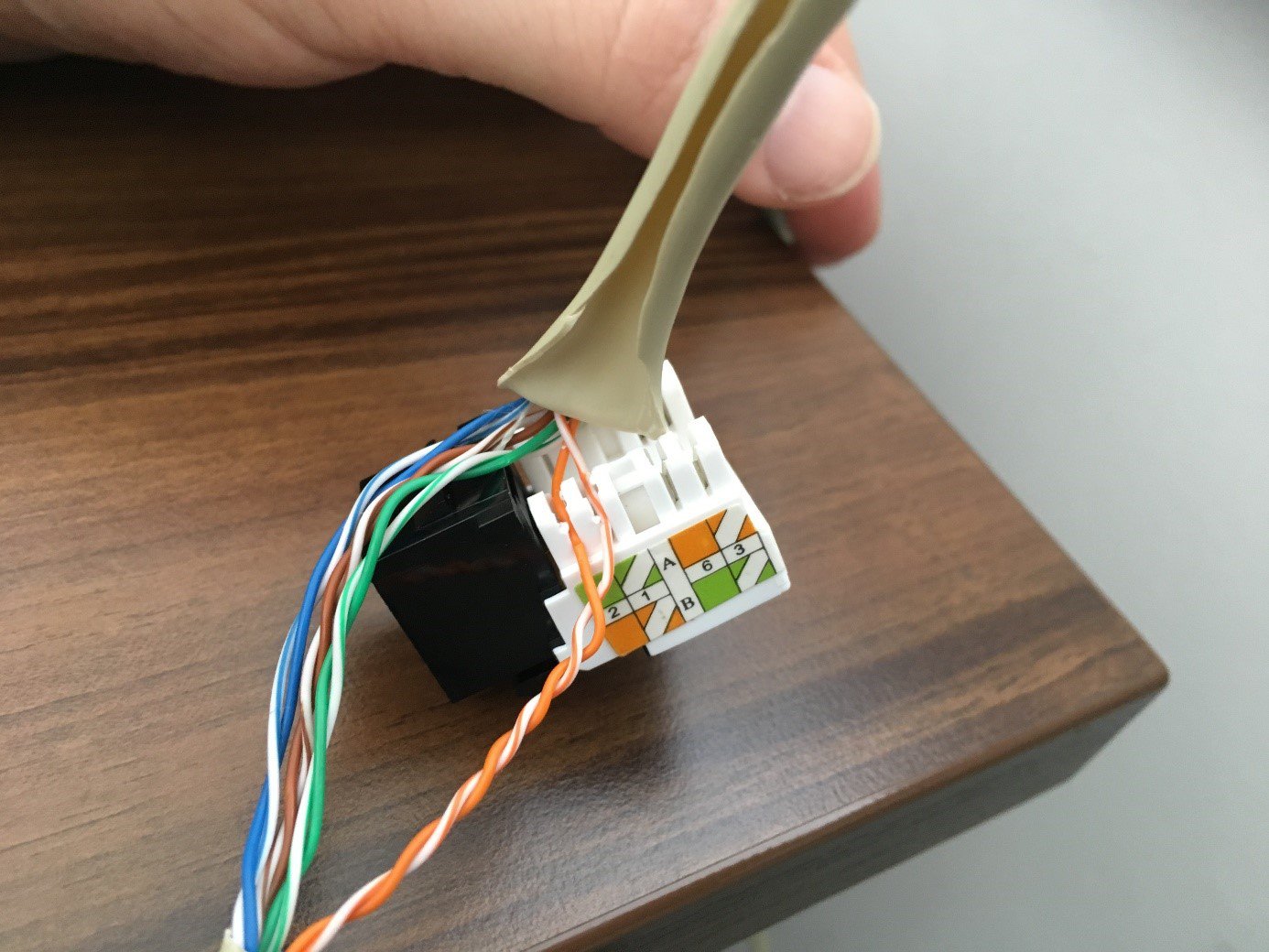
A normal communication is still going on between the user's laptop and the router. Now an attacker interferes with the path as the so-called Man in the Middle, who wants to intercept the traffic. After the attacker connects to the prepared data socket, the packets sent from the user will be propagated also to the attacker's laptop capturing the transmitted data with the Wireshark sniffing tool:

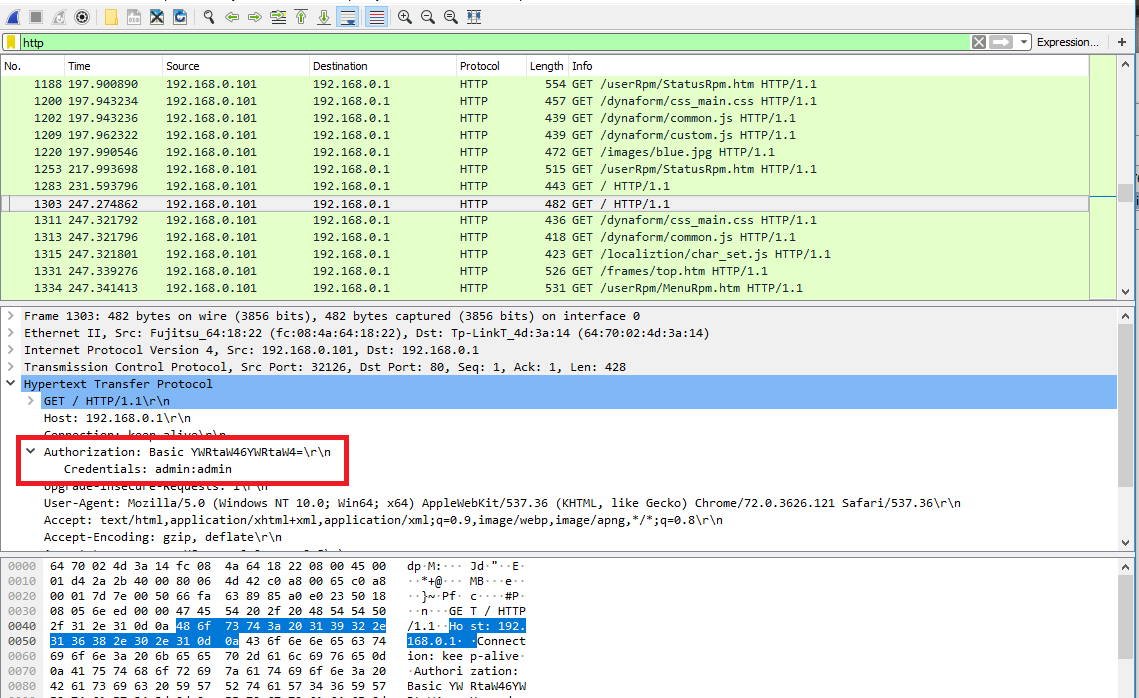
The attacker captures all data transmitted from the user to the router, in our case the user was configuring the TP-Link router and the attacker intercepted his login credentials:
After the eavesdropping is completed, we disconnect the data socket, put the cut cover back in place and insulate the cut cable. It would be best to use an electrical tape with the same colour as the cable.

How to detect the attack
Passive connections usually do not cause problems, however, devices at both ends may behave unexpectedly. For example because of changes of impedance due to the addition of a new interface or the introduction of noise. In rare cases, connection errors may appear.
In course of our testing, we did not notice any problems, suspected malicious activity or any other alerts on the user's laptop.
Taps can be detected with special tools measuring physical parameters of the cable - response since the following connection, delay time, and other parameters. However, this is not suitable for common use in big enterprises. Use of professional SW tools for traffic monitoring is recommended.
Another way to detect eavesdropping is to detect devices connected in promiscuous mode, as there are usually no such devices in the network.
Conclusion and recommendations
Wired networks are everywhere around us and are usually vulnerable, therefore, we recommend not trusting the network and using only encrypted connections. We encourage network administrators, as well as technicians, ISPs, and end-users to pay more attention to physical security and to limit access to the cables as much as possible, in order not to end up as shown below:

We also recommend using wiretapping detection modules in security tools able to prevent eavesdropping on communications. This can be used, for example, also during the Red Teaming attack, which we came across in course of our testing.
When conducting a Red Teaming project at one of our customers, we had gathered information about the company available from the Internet, but we could not access any sensitive data. The services accessible from the Internet were secured, servers updated, and so on. Access to the building was guarded and controlled, so we could not do it this way either. However, we managed to get access into the underground garages. Access to the upper floors was again controlled by an entry card, so we could only move around the garages. Here we found an unlocked cleaning room with a bundle of network cables passing through. We connected to one of them with wiretapping and we were in luck. It was a cable running from a front desk computer. It used an old reception system with unencrypted communication. We managed to capture some login credentials with the wiretapping, so during the lunch break, when no one was at the reception, we simply stepped behind the reception desk, logged in and opened the side entrance.



