Sonoff S26 Wi-Fi
And what about the security of home IoT devices? Is the level of their security still as bad? Are the manufacturers spying on their users? We have tested the smart wireless socket Sonoff S26 Wi-Fi for you, which is popular also in Czech online shops.
ITEAD, a company from Shenzhen, China, offers a range of smart home devices under the Sonoff brand patterned on the ESP8266 module with growing popularity in the DIY community. ESP8266 is a programmable SoC with Wi-Fi, UART, and SPI interfaces. A number of custom firmware is available for it and for this reason, it is suitable for many projects. We used a smart Sonoff S26 Wi-Fi socket with original firmware for our testing since it is affordable and very common in Czech online shops. The socket can be connected with the eWeLink mobile app both for iOS (v3.5.12) and for Android (v3.6.1) designed for remote control.

Initial setup
For the initial setup, it is necessary to press the pairing button for 5 seconds. The socket then creates its own Wi-Fi network. Subsequently, your mobile phone connects to it and configures the socket. The configuration mostly means sending its credentials to the home Wi-Fi network, to which the socket should connect after the setup is completed. After that, the socket is displayed in the mobile app and can be controlled remotely. However, we see as an issue that the access point which the socket creates during the pairing is protected by the publicly known password 12345678, which means that anyone can connect to it at that moment and try to configure the socket according to their wish. Furthermore, the password to the home Wi-Fi network sent by the app to the socket during the configuration is transmitted as unencrypted only with a simple HTTP request.
Online communication
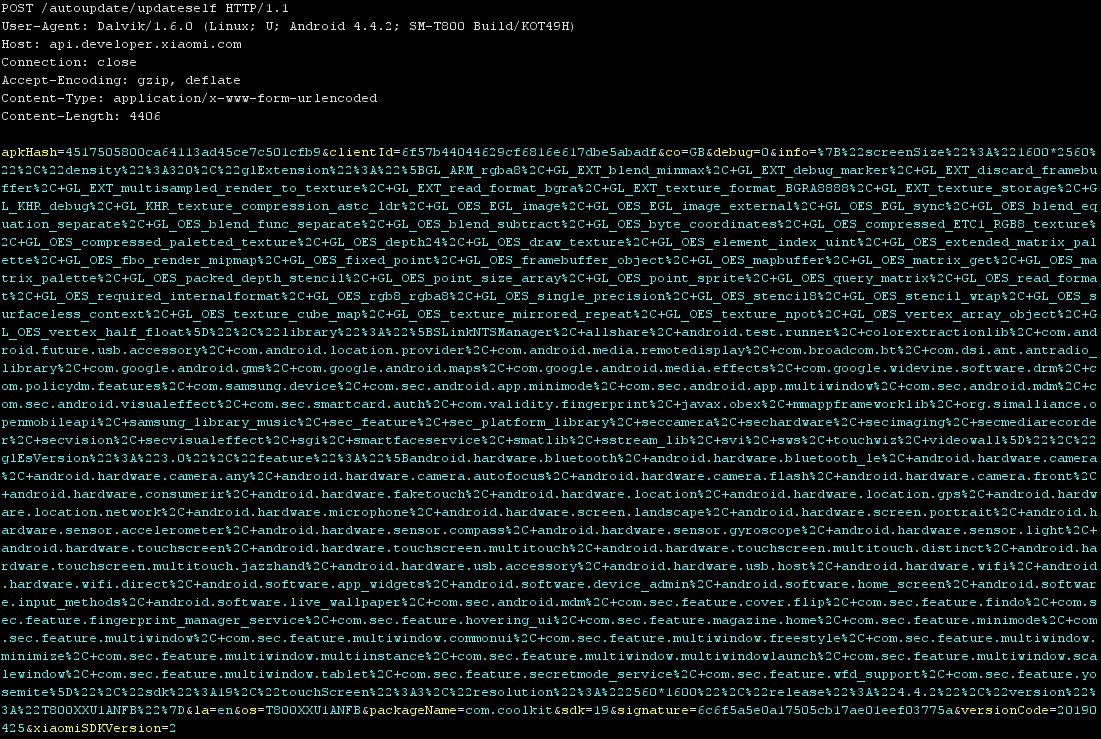
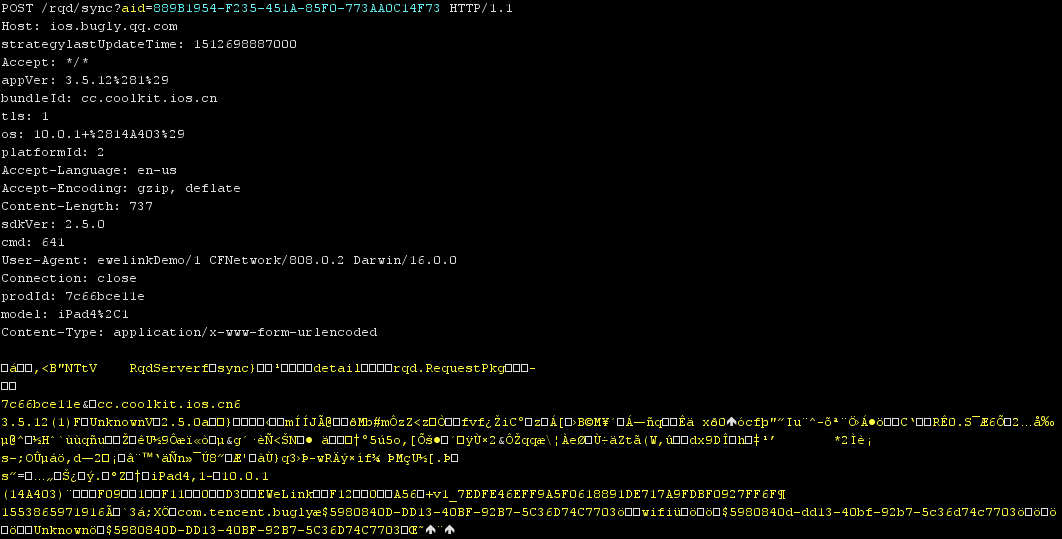
Besides the setup, there is no direct communication between the app and the Sonoff socket. All turn on/off commands are routed via Amazon AWS cloud. The connection between the socket and the manufacturer’s cloud is encrypted with TLS 1.2. Identically, the app uses encrypted communication with the cloud servers, however, when it is closed, it creates several unencrypted connections for the purposes of sending telemetry to Xiaomi and Tencent servers – this applied only to the version of the app for Android. Moreover, it must be pointed out that during the testing, the app communicated with dozens of (largely Chinese) servers. With some traffic, there was observed one peculiar thing, i.e. that even the bodies of individual HTTP requests were encrypted. These were thus unreadable, which can give rise to the speculations of what type the data sent in this manner can be.
Mobile app
After the user logs in to the app for the first time, each time it is started in the future, the user is logged in automatically, which can be a security risk – in case the mobile phone is stolen, the attacker can access the entire app without logging in. A fundamental level of protection is provided here by means of optional gesture authentication.
After decompiling the app, we found several well obfuscated classes. Due to the absence of certificate pinning in most servers communicating with the app, the encrypted parts of web request are protected only against simple attacks of the Man-in-the-Middle (MitM) type. On the other hand, for the attack of the MitM type to be successful, it would require the attacker to install his certificate on the user’s mobile phone.
Sensitive data which should be very well secured, such as the home network Wi-Fi password, the gesture unlocking the app, or the access token, are stored in the app’s data folder in a cleartext format. The app also creates several log files – and yet again, in a readable format. Here, you can find for example Wi-fi passwords again or API keys including the access token, which can be misused for taking control over the user account.
The probability that this data would be stolen is low (however, not impossible), since in order for the attacker to gain access to the application directory, there would have to be a root/jailbreak executed on the mobile phone. Nevertheless, this data can be stolen also by another malicious app able to misuse vulnerabilities in the operating system.
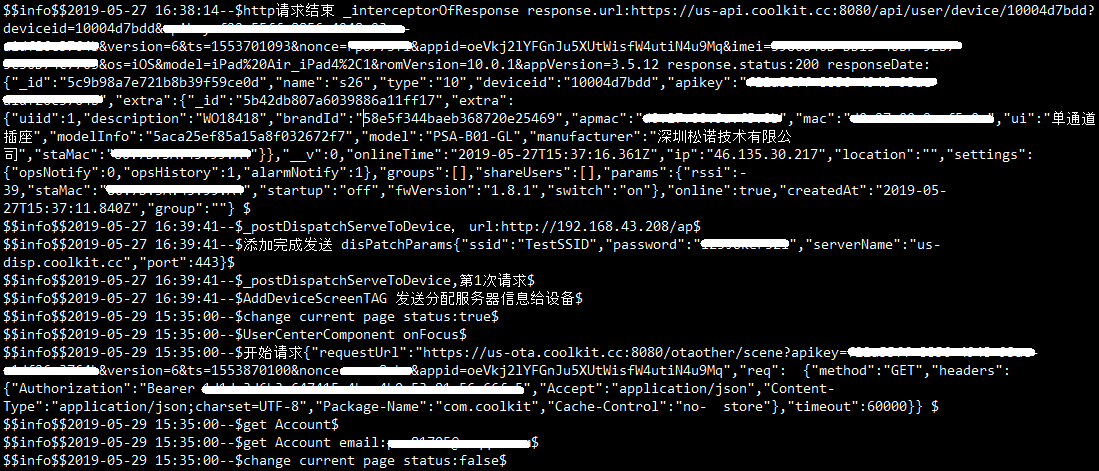
Firmware and hardware updates
Firmware can be updated with the mobile app. In the past, this option was widely used also when choosing to install one’s own modified firmware. At present, the firmware update process has been changed and third-party firmware was excluded from the OTA updates. Unfortunately, the firmware is downloaded from the manufacturer’s server with unencrypted communication when being updated. Thus there is a theoretical possibility of an MitM attack resulting in the possible foisting of a firmware to the device. Yet another possibility is a flash of firmware with testing pins, however, there are none on the Sonoff S26 board. This indicates that this may be an ESP8266 module modified by the manufacturer.

User's privacy
Following the initial doubts regarding the unsecured communication between the app and a number of different servers to which it sends unencrypted data, there is also a short description of required, nonetheless quite numerous permissions in the Android app. These go beyond the necessary functional scope of the app, which again leaves us with a suspicion that Chinese companies could be gathering and analysing our personal data.
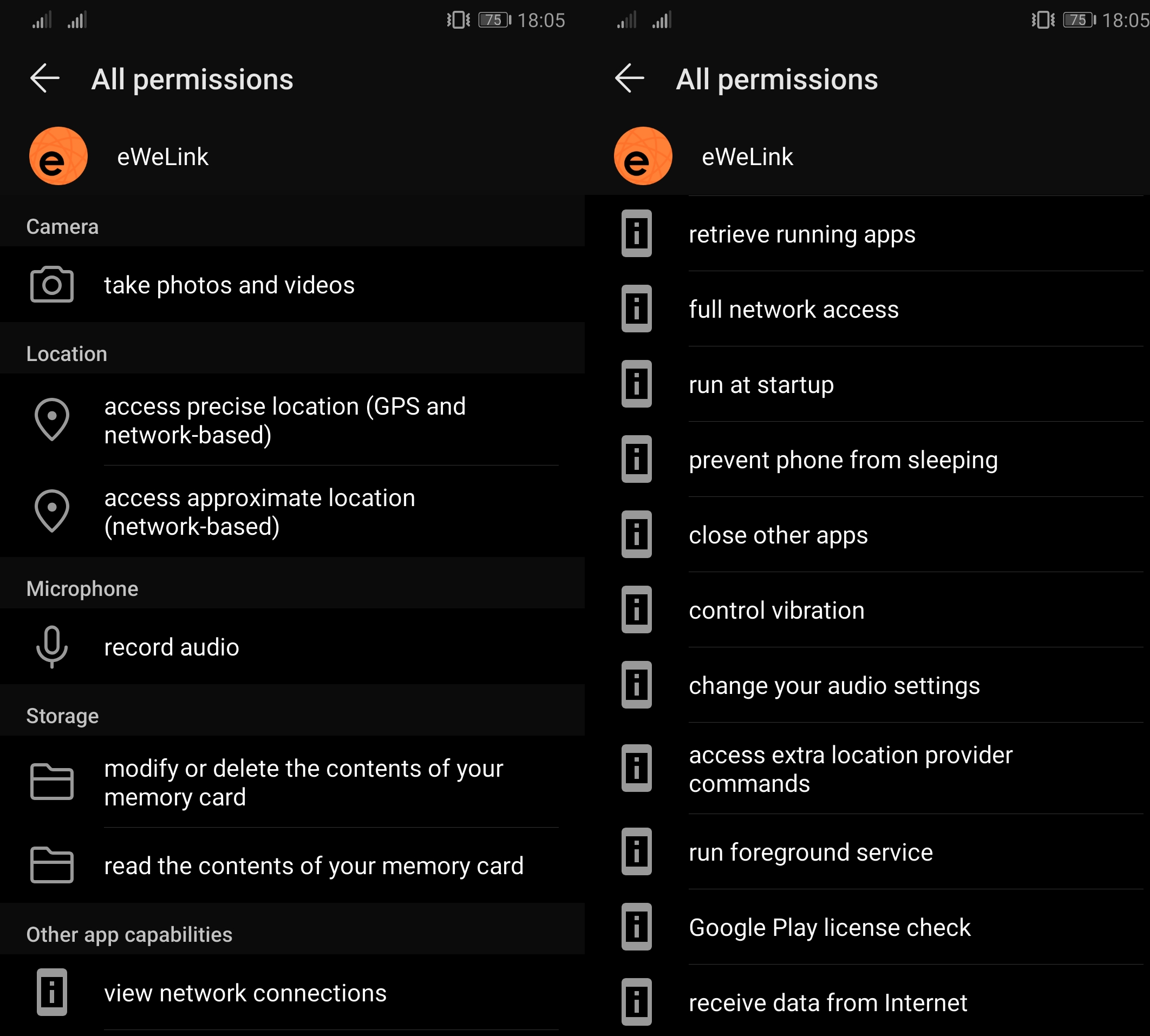
Conclusion
The pure functionality of the app and the wireless Sonoff S26 Wi-Fi socket are protected against attacks. However, the unencrypted communication to Chinese analytical services, numerous permissions of the Android app, and personal data stored in readable format cast a very dark shadow on the overall impression.



