Google Smart Lock - Trusted Face
At present, new frameless mobile phones offer biometric authentication with face recognition and it became very popular among users. But is this method secure and applicable in all circumstances? In our hacking lab, we took a good look at Google solution allowing usage of this modern authentication method even on cheap mobile devices.
Introducing biometric authentication
Mobile phone technology has taken a big step forward in the last few years. Display dimensions are growing to sizes previously unimaginable and as to the performance, phones are getting closer to desktop computers, and there is virtually nothing you cannot do with them today. However, the sensitivity of the information stored on our mobile phones also challenges their security.
New types of authentication have arisen not only for security reasons, but also due to fashion trends or the desire for comfort. However, there are several shortcomings when it comes to identity verification with a PIN or a gesture. In addition to frequent occurrence of simple codes, lengthy entering, or visible traces on the screen, you also risk that the key to your security will be revealed to strangers in the metro or on the tram. I have personally witnessed many such cases on my way to work.
Human biometrics has been the standard for more secure identity verification since the end of the 20th century. Starting with the uniqueness of the fingerprint, the pattern of the iris, the shape of the face, all the way to vocal biometrics. Use of all these identification methods is wide-spread in the world.
Due to their overall complexity and financial costs, these systems used to be implemented mainly in buildings demanding strict security. However, due to evolution and new technologies, some of these advanced verification techniques found their place in our everyday lives, including the world of mobile phones.
Uniqueness of fingerprints was the first one of biometric attributes applied in the mobile world. Most of the time, it brought the users greater level of comfort as well as better security for their own data in the phone. Although this type of authentication has its flaws, it remains a very popular and reliable method. This said, with the advent of frameless smartphones, the sensor would have to be either placed on the other side of the phone or integrated directly into the display. The second solution currently seems to be a trend for the near future, however, due to its technological challenges and longer development, telephone manufacturers began to focus on a different biometric method of human authentication, namely the face.
The start of the revolution came with Apple introducing its new flagship iPhone X in 2017. In addition to the frameless display, it also featured an infrared sensor on the front. This enabled the phone to scan the user's face with more than 30,000 points, thus verifying his/her identity. This was the first mobile facial recognition solution ever constructed in this way, though it was also very expensive. Primarily due to the great popularity and influence of products from Cupertino on the society, other manufacturers of mobile phones and operating systems were also forced to look into facial recognition.
Google Smart Lock
Another one to come up with its own solution was Google. It created a set of smart functions for device unlocking called "Smart Lock" for its Android operating system in new versions. This includes several functionalities using algorithms and sensors to unlock the screen and for more comfortable work with the smartphone.
One of these features enables to unlock the mobile phone by scanning the face verified as a "Trusted Face". This allows this type of biometric analysis to be performed also on low-cost "low-end" phones with only standard front-side photo camera. We decided in our Hacking Lab to take a closer look at this system and to verify its security.
Google: “Important: This feature is less secure than a PIN, gesture, or password. Anyone who looks similar to you could unlock your phone.”
First of all, it needs to be said that this is only an authentication method, developed and implemented by Google. It is independent and does not rely in any way on facial recognition solutions created by the actual phone manufacturers such as Samsung, Huawei, Nokia, OnePlus, and others. And Google itself warns on its website as well as at the moment of feature activation, that using the face recognition feature is less secure than a pin or a gesture. Such a statement from the manufacturer itself immediately gives a less positive impression, however, as we know from the experience, the users are not usually discouraged even by a fact like this. People are often willing to sacrifice some of their security if it brings more convenience, or if they can authenticate on their phone in the same way as people with leading flagship models.
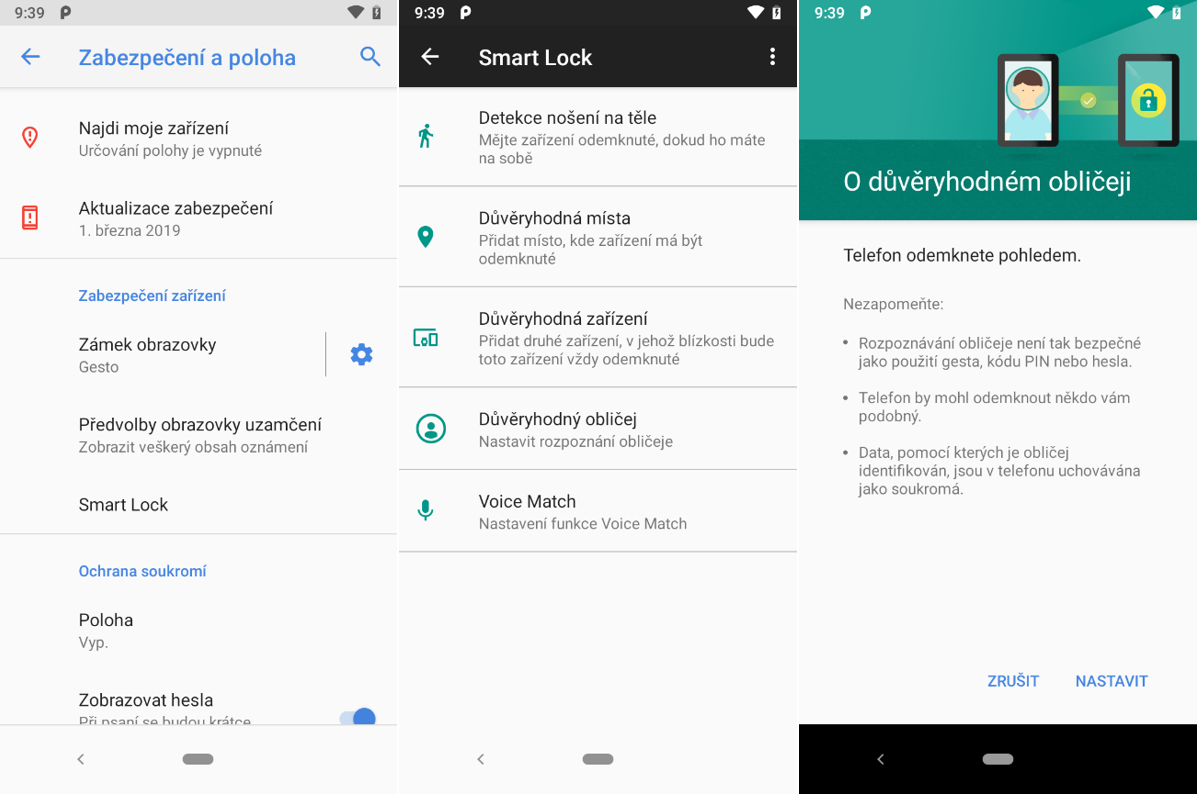
Preparation
We used two mobile phones from different manufacturers to analyse the security of this authentication method:
- Nokia 3.1 (2018, CZK 3,000)
- Lenovo Moto G5 Plus (2017, CZK 5,000)
Both devices belong to the class of cheap, commonly used phones with a purchase price under 5 thousand crowns. Neither includes a native facial authentication system, therefore, Google Smart Lock could be an extension that users could theoretically activate and use in real life. We used two identical Nokia 3.1 phones, both with different OS versions (Android 8.1 and Android 9), to detect possible improvements to face detection in more current versions of Android.
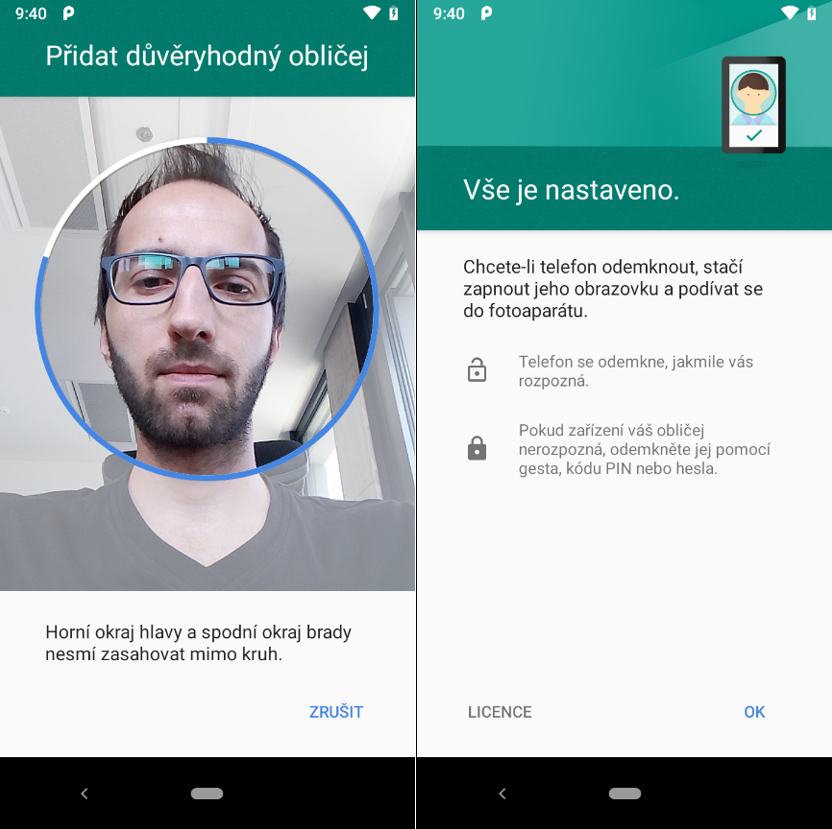
Let’s start testing
The very start, i.e. initial analysis and registration of the user's face is very trivial compared to the same process implemented in Apple phones. Mobile phone analyses a static face through the front camera for five seconds and requires no head rotation to scan the rest of the face, a change in light, or other factors which could play an important role in the following face check.
We can assume, just from the simple fact that the tested phones capture the face only with a standard front photo camera, that the scanned 3D object is analysed and stored simply as a two-dimensional image. A system designed in this way theoretically significantly reduces its actual security. Moreover, it creates many ways which could be tried to crack it. We tested it in the following three ways in our Hacking Lab.
Unlocking with someone else’s face
First, we tested the most common potential scenario to which mobile phones are exposed in public, namely the simple unlocking of the screen with a stranger's face. In this case, we used members of the penetration test team as the facial database for testing. The detection worked flawlessly on both phones, however, there were no two very similar faces in the tested sample, so from the security point of view, we can consider the result to be successful only to a certain extent.
Unlocking with a printed photo
As our second scenario, we chose a common test for which we printed a photograph of the face in colour using a standard printer. We took the photo itself with a computer webcam to simulate the front HD camera on a mobile phone as closely as possible. This test is generally the starting point for analyses of more advanced face detection methods, in which printed photographs are bent into the shape of a human head, holes for the eyes or nose are cut in them and they undergo other processes that can lead to a break in facial validation. However, none of these extensions were necessary, because immediately with the first printout, we managed to open the mobile phone just with the photograph shown to the camera on the phone. To confirm the result, we repeated the experiment once more and used a different facial expression. Subsequently, we extended the experiment by registering two additional colleagues. And also their printouts worked as sufficiently reliable objects for unlocking the mobile phone.

Unlocking with a photo in a computer
Already the breaking of face detection using a printed photograph shows that the method is practically inapplicable in an enterprise or a corporate environment. However, we wanted to see how dangerous this authentication element could actually be. Photos from the webcam can be very similar to the output from the front camera of a mobile phone, so in the next step, we tried to deceive the algorithm by presenting the image on a computer. We knew from experience that the refresh rate and radiation of LCD monitors distorts the photo or the output from the front camera of the phone, so we were not giving this experiment much chance. We used the social networks Facebook and Instagram as a source of the photos. And big surprise, when a third profile photo was displayed, the mobile phone was successfully unlocked. We repeated the experiment several times even for this scenario and tried it with other team members as well. With a total of 80 different photos, the unlocking success rate was almost 35%. In this case, the percentage to which the break was successful can be seen only as a reference number, since it is dependent on the quality of the photo test sample. In real life, it depends on what photos the attacker uses for his attempt, which is directly dependent on what images the users post on their social profiles. Thus, each user can be vulnerable in a different way.
The following video is a “proof of concept” of unlocking the mobile phone with the victim’s photo. The first person’s face is registered in the mobile phone, and the recognition of a foreign face works correctly. However, after a simple profile photo from the social network Facebook is displayed, the victim's face is recognized, and the phone is unlocked. On top of that, the example shows that in some cases, even photos of very poor quality are sufficient to break the authentication.
Conclusion
The results from the security analysis of the Smart lock feature the Trusted face by Google showed that this method is in reality not applicable for authentication purposes. The recognition algorithm is very weak with a too low "threshold", i.e. the limit above which it considers the presented face to be identical. The verification authentication method can be very easily deceived, even by simply taking photos of victims from the Internet. Nowadays, people of almost all ages create profiles on social networks and here they often share a large number of their own photos and selfies, sometimes even in a public mode. Photos exactly like these can then be used by attackers to access their mobile phones and private data.



