Car Hacking Introduction
How to control a car remotely? Or, how to unlock a car without brute force? In this article, we will answer not only the questions above, but many others too. We will take a look at the systems in modern vehicles, attack vectors on vehicles and describe the principles of the most common types of attacks.
Today’s modern cars are stuffed with electronics and control components (ECU - Electronic Control Unit). When added up, the total length of cables and wires in one car amounts to more than 4 km. With so much electronics, there can appear vulnerabilities that hackers can exploit to gain unauthorized entry to a vehicle, or they can also take control of individual control units in the car.
It must be said right at the beginning that each car manufacturer uses different protocols and algorithms to secure its automobiles. Therefore, the car hacking procedure differs for each manufacturer.
Threat model and attack vectors
Attack vectors are of two main categories, depending on the position of the security tester/hacker – i.e. whether he has gained entry to the target car or not.
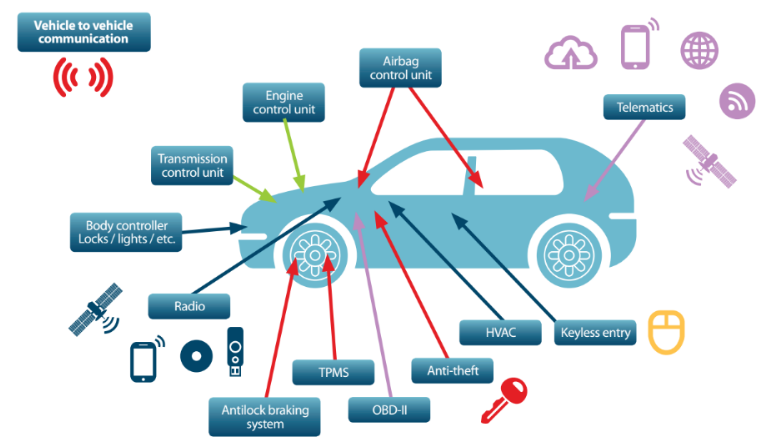
External access
- Car key and lock
- Wireless connections (mobile connection, GPS, Wi-Fi, Bluetooth)
- Tire-pressure sensors (TPMS)
Internal access
- OBD-II port (CAN bus system)
- Infotainment console & USB port
Car key and lock
The majority of car locks operates at the frequency of 315 or 433 MHz. A Software Defined Radio (SDR) can be used to tune to the required frequency for interception and the subsequent manipulation of signals.
There are 3 types of car locks divided according to the applied code: Fixed code, Rolling code and Passive systems for the so-called “keyless entry”, or keyless car entry and starting systems.
Fixed code
Older systems are using a fixed code unique for every controller. This can be easily intercepted and replied at will. After capturing only one code, the hacker gains unlimited access to the vehicle.
Rolling code
More recent systems are using a rolling code changing each time the button is pressed. The control unit is configured not to receive the same code twice.
In some cases, a Brute-Force attack can be applied on the lock, but some manufacturers implement protection against this type of attack. They implement the Antiscan feature, which prevents multiple attempts from being received on the same frequency. In this case, it is necessary to wait for a certain amount of time or apply an emergency deactivation.
These systems often do not care about the time validity of the code, so a Replay attack can be applied. The attacker will use a jammer to temporarily jam the vehicle and then turs it off after receiving a valid code. The user will have to send at least two signals to unlock the vehicle and he will have no idea that he has just became the victim of an attack. The hacker now owns one valid code to open the vehicle later.
Some locks use a challenge-response system preventing the abovementioned Replay attacks. This system needs more computing power and battery, which in turn allows communication at higher frequencies and over longer distances.
If the attacker can intercept several challenge–response exchanges, he is then able to use a Forward-prediction attack or a dictionary attack.
Forward–prediction the attack means that the attacker is observing the communication and then tries to predict what the next valid challenge requirement will be. The chance of success increases if the pseudo-random generator is weak, depending on the specific car manufacturer.
Dictionary attack can be used after a sufficient amount of intercepted communication data. An attacker can then send a set of requests repeatedly until one matches the response of the key system.
There are also other attacks, such as obtaining a code from an immobilizer, since it stays there in some cases.
Keyless entry and car starting systems
The latest type of car locks are the keyless entry and car starting systems. These unlock the vehicle without pressing a button. These locks transmit low-frequency RFID passively and send an ultra-high frequency signal when the button is pressed.
The vehicle ignores any presses of the button, until it also receives low-frequency RFID, i.e. until the key is near the vehicle. Relay Attack can be used as a primary attack on this type of key.
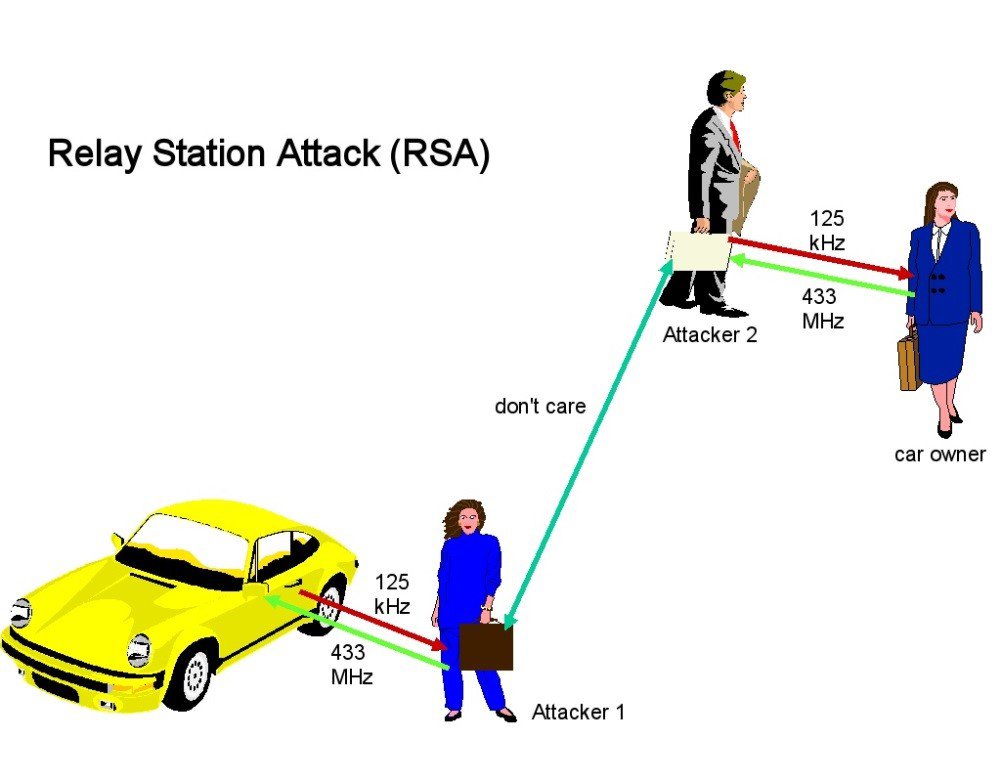
It takes two hackers and two radios to execute this attack successfully. One attacker places one radio next to the vehicle and the other places the other radio next to its key. The radios exchange signals with each other and the attacker is able to open and start the car. Hackers can use any signal between each other – even the mobile network. Both hackers must be a few meters from their respective targets to obtain data, however, antennas can be used to amplify the signal.
In these cases, all alarms in the car become obsolete, since the car trusts the signal and is not able to find out which source sent out the signal. The so-called sleeping keys can protect you against this type of attack. The signal stops transmitting if the key remains in one place. Some car manufacturers use sensors inside the car to determine the location of the key. However, these protections are not available in older models.
Key sleeves working on the Faraday cage principle are a universal solution to these problems.
Tire-pressure sensors (TPMS)
Tire sensors are sending an unencrypted radio signal with information about the pressure in tires and wheel speed to a receiver connected directly to the ECU unit, which is part of the CAN bus (see more information about the CAN bus below).
Since 2012 (since 2008 in the USA), all new passenger cars manufactured in the European Union must be equipped with TPMS, and this was the beginning of attacks targeted at this technology. Although the signal transmitted by the sensor itself is weak, a low-noise amplifier or directional antennas can be used to capture the communication across the road or alongside a moving vehicle.

The sensor transmits data every 60 to 90 seconds. Some vehicles need to be moving for the sensor to be activated, while others are transmitting the signal even if the car is at rest or, on top of that, turned off; therefore, the hacker can send a wake-up signal to force the sensor to respond at the frequency of 125kHz.
In order for a hacker to be able to exploit security vulnerabilities in these sensors, he must first eavesdrop on the communication through the SDR, then the communication needs to be filtered and demodulated. This way the attacker obtains an encoded signal, which he must decode with the correct algorithm. The decoded packet contains a unique ID as well as the actual data.
There is no signal authentication in the receiver. Thus, after reverse engineering of the packets, the attacker can switch the radio from the receive mode to the transmit mode and start sending modified packets.
In addition to spoofing false information about the condition of the tires, the hacker can force the car's pilot lights to turn on or switch off the receiver completely. After this type of shutdown, the vehicle requires servicing to reset the unit.
Subsequently, the system can be overloaded with wake-up signals, causing the battery to go flat. Moreover, the sensor can also be misused for tracking the vehicle by strategically placed receivers (e.g. garage entrance).
OBD-II port (CAN bus system)
Since 1993, the CAN protocol has become an international standard for common vehicles (ISO 11898) and it has been mandator for all cars manufactured in Europe since 2001 to have the CAN bus installed. Each car manufacturer can use slightly different protocols on the CAN bus and the frequencies used in communication.
All important data on the status of the vehicle is transmitted to the CAN bus. Cars have several control units (up to 70 ECU) on the bus. The CAN protocol is broadcast, and each unit sees all packets, so it is not possible to determine which unit or attacker sent the given packet.
Units evaluate the relevance of a message according to the so-called Arbitration ID specifying the ID of the unit for which the message is intended. This ID also determines the priority of the message – a lower ID means a higher priority. 6 zeros in a row indicate a high priority error. The principle of a DoS attack lies in sending 32 error messages of this type in succession causing the ECU to switch OFF.
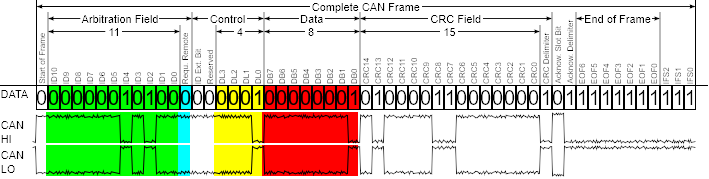
The actual data is another important field in the CAN packet. It contains specific information such as the current speed and distance of the objects when parking. According to the standard, the OBD-II connector is usually located under the steering wheel and easily accessible. This port provides full bus access.
Car manufacturers use different protocols on the bus, so the attacker must adapt the data sent to the ECUs for each car.
There are a number of OBD-II adapters available for USB, Bluetooth, Wi-Fi or with a GSM module and because, as we mentioned above, the CAN protocol is broadcast, all adapters on the OBD-II port therefore can see all communication on the CAN bus. Third-party data processing software can be used with these adapters, which opens up the possibility of creating your own application designed purely for the implementation of attacks. The actual hacking of the CAN bus requires eavesdropping on the communication on the bus and then it is also necessary to take additional steps in the form of reverse engineering, which requires a sniffer and other software capable of CAN packets dumping.
The hacker who can get access to the OBD-II port and performs the above-mentioned steps, gains control over the CAN bus, i.e. over important vehicle functionalities. Detailed description of the CAN bus hacking deserves a separate article and goes beyond the scope of this introduction.
Infotainment console & USB port
The infotainment system usually runs on Linux and Windows CE. If the environment is virtual, Android system also works.
The console offers a wide range of attacks. There are USB, CD and DVD or audio jack for the physical ones. And Bluetooth, Wi-Fi, GPS, and mobile network for the wireless attacks. The infotainment system uses the CAN bus as well, but it is separated from the primary backbone containing important vehicle functions.
The most common method of attacking the infotainment console is through system updates. Before this type of attack, it is necessary to find out which system is running on the console and how it is being updated. The procedure is a little different for each car brand. Different architectures, upload methods, and file systems are used. Some updates are protected by a digital signature and there is a risk of "bricking" the system (firmware or hardware damage due to incorrect settings) too. For these reasons, it is recommended to modify, for example, only the logo of an existing update to test the functionality.
Other vulnerabilities include access to the debug screen or an undocumented backdoor.
The USB port can be used for updating the firmware of the internal chips. The firmware can be modified to include the required vulnerabilities in the system (for example, when hacking a Jeep Cherokee in 2015).
Remarkable hacks of the past
Universal mobile app
Automobility, a Canadian company, has developed the MyCar system consisting of a device with GPS, a mobile internet connection, and an application. The software is distributed under other names such as MyCar Controls, Linkr and some others.
One can see the status of the vehicle in the applications and they allow locking, unlocking, and starting the car, killing the engine and finding out the car’s location.
A hacker nicknamed Jmaxxz discovered several vulnerabilities in the mobile app last year. The result was that he could see and possibly take control over some 60,000 cars. He could see brands, models, and years of production, so he could choose the car he wanted. The reason behind was a bug in the app in the form of hard-coded administrator credentials, which allowed him to access the company's backend. Other vulnerabilities included SQL Injection and Insecure Direct Object Reference, which would also give him access to the abovementioned information and allow him to send commands to other vehicles.
2015 Jeep Cherokee
Probably the most famous car hacking took place in 2015 on a Jeep Cherokee, where two hackers remotely controlled a car in traffic on the road. See a brief summary of the process below. The full article is available: here.
For this type of hack, it was necessary to know the IP address of the vehicle. This can be either randomly selected from the range available to the manufacturer, or an automated worm can be used to go through all IP addresses and to hack all cars. If we want to find out the IP address of a specific car, we can scan the network and find the IP address according to the VIN number or GPS (but this is time consuming).
Through the open port Sprint of the network 6667, they were able to take control over the OMAP chip (infotainment console communication chip), then uploaded the SSH public key and configuration file, and started the SSH service and thus got the RCE (Remote Code Execution) on the OMAP chip.
At this point, the attackers had the infotainment unit Uconnect under their control and could play, for example, with the radio. However, this was not enough to get a complete control of the vehicle and therefore they used the OMAP chip to flash the second chip - the V850 - as well with modified firmware. The V850 can communicate with the CAN bus. Through the modified firmware, they were able to send CAN packets and control important vehicle functions and deactivate it as shown in the picture.

Conclusion
With the growing volume of electronics in cars, the risk of vulnerabilities in control units, especially in smart and autonomous vehicles, is constantly increasing. For this reason, it is necessary to ensure the highest possible degree of electronics and software security – and the fact that the safety of the vehicle is closely linked to the safety of passengers in this case is not the only reason. Car manufacturers are trying to fix the identified vulnerabilities; therefore it is important not to skip manufacturers' convening actions and software updates.



