Social Networks, New Platform for Social Engineering Attacks
Social networks allow us to connect with people from all over the world in almost no time. These platforms have changed the way we interact with others. In earlier times, the first thing we did in the morning was to buy a newspaper to see what happened in the world around us, but today, most of us just check our social media accounts. This is our connection to the world today. Just one click and we can see pictures from exotic places and watch videos of small cute kittens. These networks connect us with the world in a way previously unthinkable. But along with all the goods things they offer (speaking mostly about the kittens), there are also coming threats and new attack vectors that evil social engineers would be happy to use to their advantage. Nowadays, it is therefore necessary to be wary of the ever present scams on social networks. Now, let’s take a look at the most common scams used by social engineers, and also how to defend against these types of attacks.
Social network scams
When we think the word "scam", many of us will recollect the famous scam with the Nigerian prince. Most of us have heard of it and there are even many jokes about it. And yet this scam was very successful at the time. Is it still as successful? Probably not, a large number of users are already quite technically proficient and also better educated to recognize these obvious patterns of phishing emails. But hand in hand with our progress in education, the scams are improving too.

Social network scam is becoming more and more popular. Active users of Facebook, Instagram, Snapchat, or other social networks are prone to becoming victims of fraud, due to their large public exposure and sharing of personal information.
Various types of social network scams are using social engineering techniques to quickly build trust between the attacker and the victim.
This includes for example the following techniques which subsequently make the scam credible:
- Misusing information about the target’s favourite topics;
- Open-end questions (What did you do at work today?);
- Identifying with the target of the scam;
- Presenting himself as unselfish;
- Others...
Due to these developments, we must also change the way we think about these scams in order to better protect ourselves and our loved ones from these threats.
A look behind the scenes of social network scams
We already see after the opening that the threat is real and for understandable reasons, also very popular among social engineers.
As the saying goes: “A disease known is half cured.” The second half then comprises getting to know some of the most popular scams circulating on today’s social networks.
The following are the most popular attack vectors:
- Social network phishing;
- Love on the Internet;
- Quizzes.
Naturally, this list is not exhaustive and there are other forms of attacks, but these three are among the most common ones.
Social network phishing
The way social network phishing works is similar to common e-mail phishing. You receive a message from one of your contacts that requires clicking on the attached link under some pretext. However, what you don’t know, is that your friend’s account was compromised some time ago and that the message is sent by an attacker.
Or, you receive a friend request from your long-term friend. According to his profile, everything is fine and it’s really him. You are not aware that you would remove him from your friends, but anything is possible (he has a new profile, he deleted me by mistake etc.). You accept the request and all seems well, however, what you don’t know, is that your friend’s profile is not secured and attackers downloaded his pictures and data and created an identical profile.
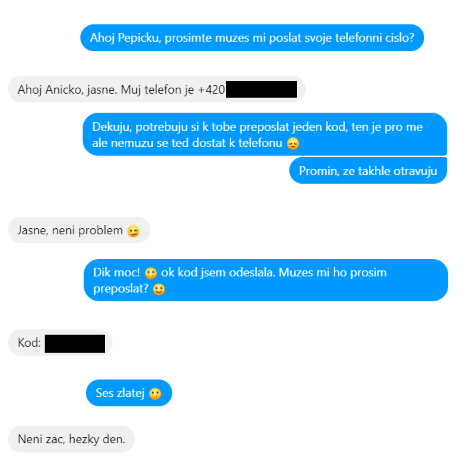
In the Czech Republic, the m-payment scam has been and still is popular. Meaning that an attacker asks you if he can forward a code to you which he then needs you to read to him.
And how this type of attack works? To model this situation, let's imagine two users, we can call them e.g. Annie and Joey.
One day, Joey receives a friend request from his friend Annie. Because they have known each other for a long time, Joey accepts the request and he no longer thinks about it.
The day after, Annie sends him a message asking him for a phone number. She allegedly lost her phone and needs to send one message to Joey with a code that he should read to her.
Because they are such good friends, Joey does not question this situation and sends his phone number to Annie. In no time, he receives a text message on his phone with the code for Annie.
Joey forwards this code to Annie; she is really grateful for his help and thanks him. Joey thinks that everything is over.
But in the following month, Joey gets an unusual statement higher by CZK 1,300. What Joey did not know was that the code Annie wanted from him was in reality a confirmation of m-payment.
Because the person who was writing to him was not actually Annie, but an attacker who created an identical profile, since Annie shares all her data as public.
This type of attack was immensely popular on Facebook social network in 2017, nowadays, it is moving primarily to Instagram.
How to defend yourself against these attacks?
- Beware of messages that contain various types of typos, or which seem unnatural in any way to you.
- Under no circumstances do not recklessly click on any links or share with the other party any codes sent via SMS to your phone number.
- Remember that you have no idea of motifs of the people who want to follow you on social networks, or, alternatively, send you a friend request. It is very likely that their motives are completely innocent. However, do not forget that if you allow strangers to connect with you on a social network, you give them access to the personal data contained on your profile along with the actions you take (commenting, liking, posting, etc.)
Love on the Internet
These scams are unique because the attacker tries to parasitize on the human need to feel an emotional connection. The attacker establishes contact with the victim and in course of the scam tries to create feelings of love towards himself on the victim’s part.
As the target's infatuation with the attacker deepens, the attacker gains some form of control over his victim. Then the attacker, under various pretexts, starts demanding certain amounts of money from the victim. These demands may increase over time until they reach an amount that the victim is unable to provide. At that moment, the attacker ends all communication with the victim and sets out to look for another potential victim.
This fraud is particularly cruel, since it usually parasitizes on middle-aged women or targets single mothers who have been without a partner for a long time and are not in the best of situations. The attacker picks such a victim, and then pretends to be a wealthy foreigner, telling them compliments and sending amorous messages. Thus he uses their emotional deprivation, or in case of single mothers, their need to provide their child with a father who will take care of them.
And what methods an attacker uses when searching for his victims? With key words. All of them are single, or they even share their status on Facebook together with melancholy, even depressing posts.
This type of attack happened in the Czech Republic as well, specifically in February 2019 server idnes.cz informed about these scams and their victims. In some cases, the victims repeatedly sent money to the con man and the total payment has amounted to CZK 2,000,000!
How to defend yourself against these attacks?
- Ask specific questions and note any discrepancies.
- Be suspicious at all times. Does the person look too good in the profile photo? Use a Google web search, which can search for an image, and google the picture! This way you can determine if the person copied the photo from somewhere on the Internet.
- Always beware of people who keep making excuses for not being able to meet in person (permanently on a business trip, a wealthy foreigner from another country, a soldier, etc.), or are always postponing a scheduled meeting.
- And most important of all. Never, under no circumstances, send money to someone you have never seen in person and you met him/her online.
Quizzes
A popular pastime which often looks quite innocent. Which one of us has never wanted to find out what character we were in the Game of Thrones, or what will be our last sentence before death, etc.
Unfortunately, scammers may use these quizzes to install malware or collect personal data. And even if the quiz is legitimate, personal data is collected about us, which can be used for targeted advertising.
The best way to defend yourself against potential scam is to simply not fill these quizzes. Nevertheless, if you still need to know which Avenger character you are, read the privacy notice, or, alternatively, the notification how your personal data will be processed and for what purposes it will be used.
Most of these quizzes will inform you that by participating in this quiz you agree to the terms of use of the website with the quiz. In these terms of use, you will subsequently discover that such consent allows various third parties access to your friends list, your e-mail address, and others. Then it's up to you to assess whether these third parties really need access to this data.
Be watchful but not poranoid
The easiest way to understand the risks associated with social networks is to realize how useful this information can be to an attacker. If you understand what the attacker is looking for, you can defend yourself effectively.
Now, stop for a moment and look at your social network profiles through the eyes of an attacker. Is your birthday or any other anniversary shared publicly? Does your profile say where you work? Did you attach geological metadata to a photo from your favourite coffee shop last week where you had your favourite cup of coffee and dessert, just like every week?
This is exactly the kind of information that attackers are looking for. This information may seem unimportant in itself but by interconnecting it, a fairly accurate picture of your life and habits can be created, and an attacker can easily misuse it in a targeted attack through e-mail (spear-phishing) or phone (vishing).
Fortunately, there is a fairly simple way to prevent this information from falling into the hands of an attacker, which is your profile security setting. Due to the option to set your accounts on social networks as private, an attacker cannot access this data through social networks, at least not so easily.
Then, it is necessary to check these settings regularly, as social networks are very often updating the settings for user data sharing to increase security. As a result, your settings may be affected without your knowledge.
In conclusion, I would like to say that it is my hope that knowing these most well-known types of attacks that are currently occurring on social networks will help you to be more cautious if you encounter any of them in your life. And if you still do fall victim to a similar attack, do not hesitate and report it to the social network on which it happened. This will help with an identification of the attacker on the social network and possibly prevent other people from becoming victims too.



